Venmo, a social payment system, defaults to public disclosure of payments made on the system.
https:...
Read More
It has come to my attention that one of Paul Asadoorian's Security Weekly broadcasts is titled Appli...
Read More
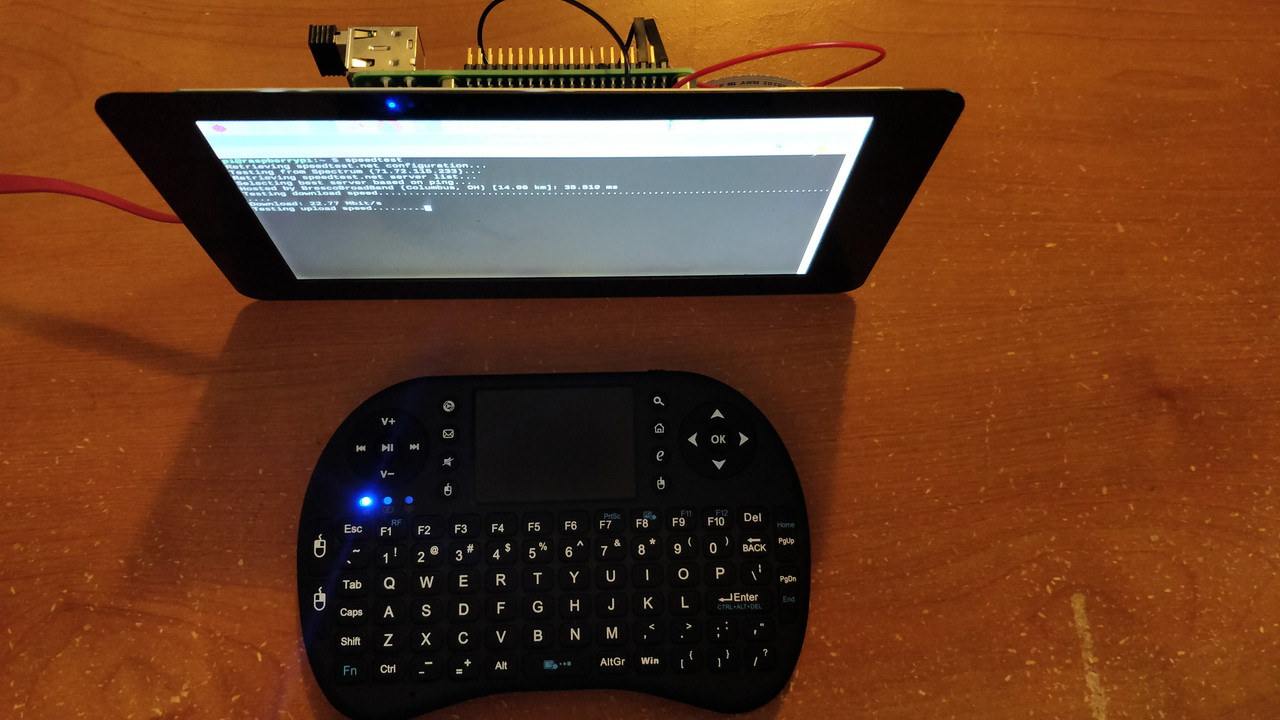
For my home internet, I have one choice - Spectrum, née Time Warner Cable. I don't comp...
Read More
npm is a dumpster fire. Yet another malicious package discovered that it automagically brought...
Read More
LTE has a bug. Who knew? One more strike for IoT devices, methinks.
https://arstechnica.com/in...
Read More
It's the "Bill accidentally skipped a week" edition. I didn't even DO anything last Sunday, I...
Read More